S4 Proof Of Concept (POC) Pavilion

Purpose: Demonstrate to the S4 attendees OT security products attempting to solve an asset owner problem.
Approach: Simulate a proof of concept (POC) project, installation and demonstration on a manufacturing plant. The Pavilion sponsors must install and demonstrate their solution on the OT environment provided and run by Booz Allen.
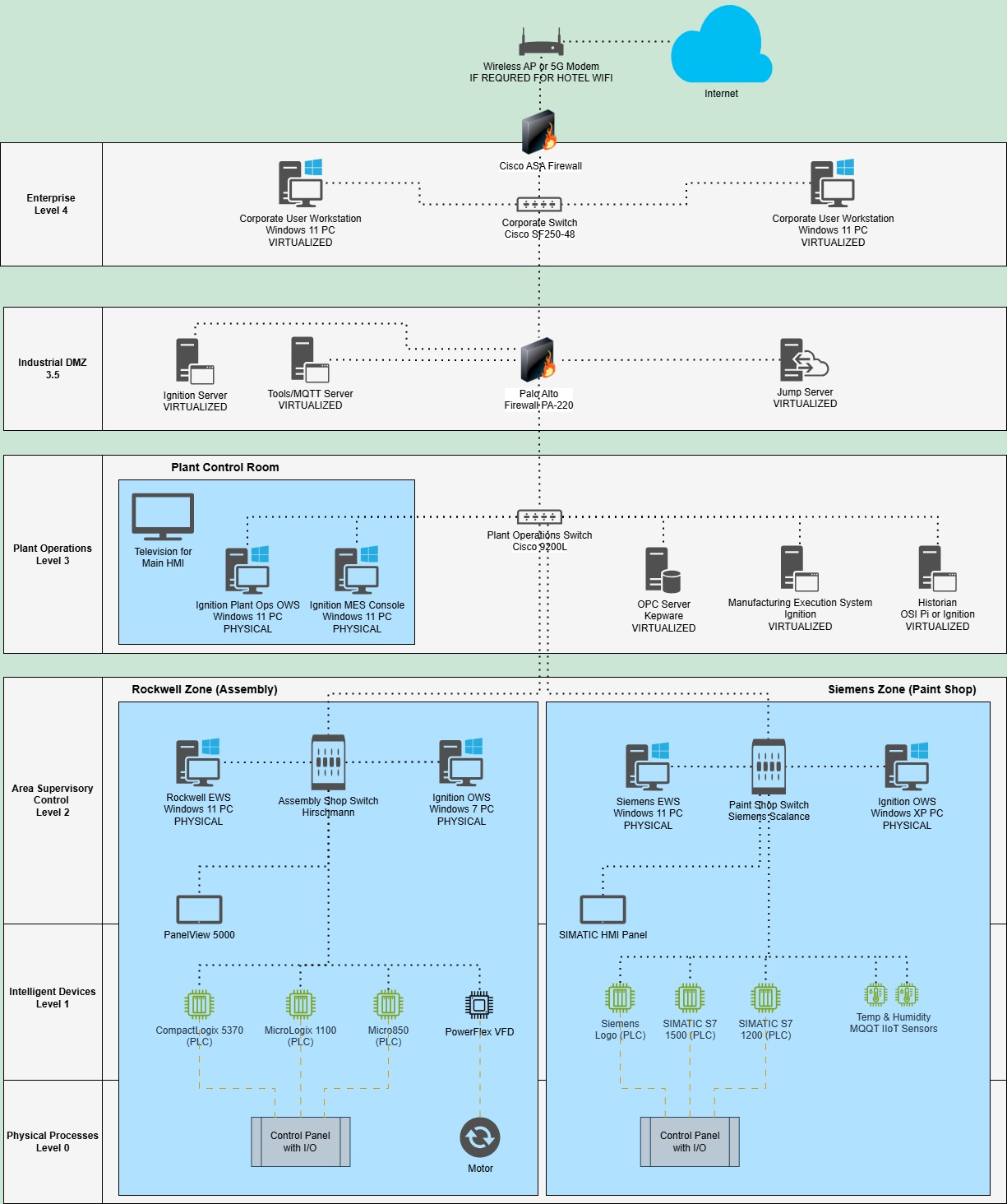
Pavilion OT System: A highly realistic manufacturing system. It include the MES, SCADA, HMI and PLC levels of the manufacturing automation stack. The primary vendors in the system are Inductive Automation, Rockwell Automation, and Siemens (see network diagram below).
Four Questions For The POC Pavilion Stage Presentation
- What problem is your solution solving?
- What are the criteria to determine if your solution is successful?
- How long did it take to implement the solution?
- How much does the solution cost at deployment and annually?
The eight POC Pavilion Participants will be demonstrating their solution in their exhibit and once live on the POC Pavilion stage. There’s nowhere to hide, and the Participants will answer questions from the emcee and audience.
| Vendor | Problem | Success Criteria |
| Cisco |
1. How can we prevent unauthorized or unnecessary communication in our OT zones without rearchitecting the entire industrial network? 2. How can an analyst in the SOC receive and analyze OT events in conjunction with IT events? |
1. Demonstrate that unnecessary and unauthorized communication is prevented in the Assembly Zone. 2. Demonstrate unnecessary and unauthorized communication attempts in the Assembly Zone are presented in Splunk along with other OT and IT security events. |
| Claroty | How do we know what cyber assets are in our OT environment, the vulnerabilities in these cyber assets, and which actions will most effectively reduce related risk? |
Objective 1: Provide a detailed asset inventory that can support the engineering team’s understanding of what assets are on their network, and demonstrate that the approach we take can be scaled across their entire estate to optimize insight while minimizing time to roll out and cost to implement, as measure by: ● Visibility Quality > 85% Excellent Visibility for the OT assets in scope (defined below) Objective 2: Demonstrate that the solution can accurately identify vulnerabilities and exposures (non source code risk factors) comprehensively and accurately, the risk implications to operations, and the prioritized actions to mitigate the risk, as measured by: ● Correctly identifying 85% of the KEVs and easily exploitable exposures on the assets deployed in the environment |
| Dragos | How can we identify critical assets, vulnerabilities in those critical assets, and the risk associated with the vulnerabilities? How can we identify the best way to mitigate the identified risk? | The solution is successful when true operational risks to the network are highlighted through vulnerability and lifecycle management, asset communications, or notifications. |
| Elisity | How can we prevent unauthorized or unnecessary communication in our OT zones without rearchitecting the entire industrial network? | Demonstrate that unnecessary and unauthorized communication is prevented in the Paint Zone. |
| Frenos | How do I assess my security posture in my OT environments and know which risk mitigations to prioritize? | Cyber Posture Measurement of total exposure: – Count of potential paths – Count of assessed paths – Count of paths with access – Count of paths to crown jewels Exploitability – TTP Prevalence – Vulnerability Exploitability Risk Mitigations Mitigation prioritization score Control Opportunities – Segmentation Score – Visibility Score – Vulnerability Score – Misconfiguration Score Risk Reduction Opportunities – Risk reduction percentage |
| Salvador Technologies | How do we quickly recover our OT computers to a known good state if they are compromised or corrupted? | Impacted OT computers are recovered in less than 5 minutes after the recovery command is sent. |
| ServiceNow | How can we import identified cybersecurity risks and manage the workflow to mitigate those risks? | 1. OT cybersecurity change orders and incident responses can be triggered and routed based on inputs from multiple data sources, including ICS assets and other security solutions. 2. Workflows are available to manage not only security activities, but also the physical plant actions related to security responses. 3. Change orders and incident responses can be tracked, filtered, and reported on from a unified dashboard. |
| Xage | 1) How can we allow access to our OT environment, but ensure that access is only granted to the right users, for the right assets, and only when they should have access—without impacting productivity? 2) If our vulnerable devices cannot be or are not patched, how can we ensure that they do not become threat vectors used in breach? |
1) Unauthorized users have no access. 2) Authorized users are allowed to access selected systems and blocked from other systems. 3) An authorized user can be restricted by capability on a system. For example, changing some points, but not others. 4) An exploit that would work on a POC cyber asset with unrestricted access is blocked. |
POC System Documentation And Process
Here are two documents that will help you understand what will happen in the POC Pavilion.
The Booz Allen team put together a document than mimics what an asset owner would provide a vendor coming in to install and perform a POC with their solution. It actually exceeds what most asset owners provide in detail and accuracy. We are simulating an asset owner with a mature OT and ICS security program.
S4x26 POC Pavilion – System Information Document
The second document covers the process and logistics for the Pavilion from the delivery of these documents through the on-stage live demo of the solution attempting to solve the identified problem.
POC Pavilion Network Diagram